For the last week we went over the code again to make sure there are no errors in any way shape or form. Then we finished up by making the slides for the presentation. This was by far one of the most difficult projects that I have made in my days of Binus, but overall it was do able and pretty proud of the product that came out of it. It was a great learning experience in machine learning. The last thing we did was upload the code to GitHub and made the demonstration video that was required for us to make.
This week we are going to touch up on the code that was previously made the week before. In order to make it more readable and easier to understand we changed things around so that we can explain it better to the class. The code that we made was only able to filter based on movie titles, but we felt that was not enough so we decided to add some other features to it. The thing that we added was that you could base your filtering on genres and directors to give the program more variation rather than just filtering by titles. After completing this step all that is left to do is do prepare the demonstration video, the presentation slides, and uploading everything to GitHub.
We have finally found a complete data sets that consist of many movies and its appropriate datas that are needed for the project. We started this week by watching over the video again that will help us to bring this project to life, followed by brushing up on some python skills. Then we finally started to code using Colab by Google so that all of the libraries that are used are already there. No need for further installations which is really nice. We found a great source that will help us for this project and later will be cited in our presentation. We got the content based filtering to function with minimal functionalities, but in the following week we will continue to improve and if possible add our own features in order to make it more interesting.
This week our group met up to do some research in finding a well documented movie recommendation program to see what types of filtering or algorithms that are used. It was found that the most commonly used filtering system for these type of programs are popularity based filtering, content based filtering, and collaborative filtering. Which is great for us because content based filtering is what we planned on doing so we are finding some sources in order to implement that type of filtering into our project. Watching some YouTube videos as well in order to understand more on this type of filtering and Also finding a large data set with lists of movies and its appropriate data.
After the mid exam our group conducted a research between types of filtering in order to make our movie recommendation program. We as a group, decided to do a content based filtering program. In this type of filtering the user will be asked to input a movie title, genre, or director. Then it should list out movies based on the user’s input. But the goal for this week is to find out more about this type of filtering and find a way to implement it into our project and make it come to life.
For this week I have been doing some research to as how we are going to start and execute this program that we are making. First I read some basic Python documentation to brush up on my coding, since it has been a long time since I have used Python. Then one of my group members Tom, sent me a link for a video that he recommended for the group to watch. Which was an a guide on how to build a movie recommendation program. After doing so I continued to brush up on my python and slowly but surely. But for the following week our group decided to pause the project considering that we have mid-exams coming up. So as a group we decided to focus on our exams and study hard and as soon as the exam is over we will pick up right where we left off.
Our group consists of 3 members: Krisie Aurelia, Tom Herbin and myself. We decided to do our project on a machine learning movie recommendation program. We chose this idea because all of the other groups in the class decided to make board games with machine learning. We have been making silly game programs since the first semester of Binus and we find that to be useless and won’t be applicable in real life. So with that we chose to do something different than the rest, although it may seem a bit harder but the challenge is worth it. So this is our basic overview of what our project is going to be. Its going to be similar to most movie recommendations program but we will do our best to add features that have never been used before.
In this final blog we learned the two types of documentation when creating a report for penetration testing. One is a technical report which allows the client to see the methodology used during the testing. Also it tells the client the lists of vulnerabilities as well as the risks of having them. After listing the them you also tell the client the result of your test. The other report that we learned was called an executive report. This type of report is quite simple. It just states the executive summary and the methods that are used to execute the penetration test.
In this blog we will discuss a tool called Nikto. Nikto is a website vulnerability scanner that scans against web servers for potential outdated servers, services and software version’s hidden presence of multiple index files, etc. It works by making requests to the server, evaluating the responses in return.
The basic syntax of using Nikto : nikto -h domain/host name/ip addr
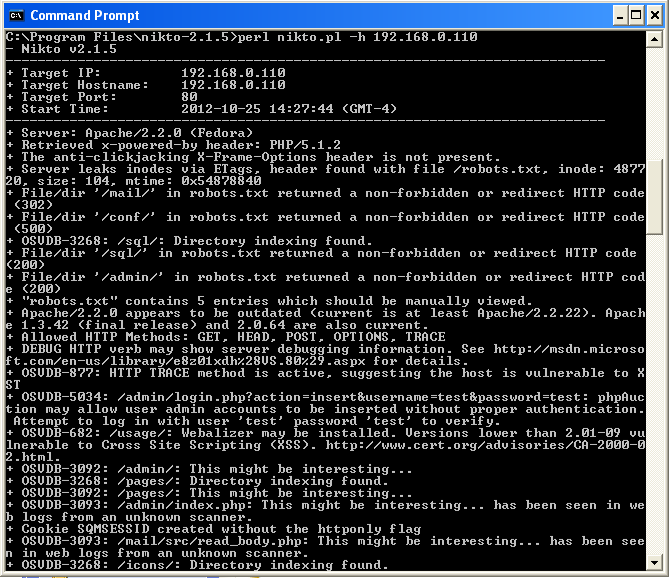
in the picture above you can see all of the web Vulnerabilities that is on the server that you are trying to exploit. This tool can be very useful when trying to gain access to a website because you need to find the weaknesses first before actually gaining access.
In this blog we will discuss of how to maintain access and why that is important when gaining access. Let’s talk about why it is important to maintain access. Here is a list of reasons of why maintaining access is very important. First you don’t need to reinvent the wheel, previous Vulnerabilities could be patched already, Sysadmin makes it harder to break into the system, and saves time for future purposes. Then we ask ourselves, how to maintain access while already inside the system. Well it is quite simple some ways to maintain access is to create OS backdoors, Tunneling or web based backdoors. Backdoor is a method that allows the hacker to access the target without any authentication and remain undetected. Tunneling is a way to get access through a server by passing a certain protocol by using encapsulation off a network.
Recent Comments