In this blog we will discuss about Privilege Escalation. Once gaining access to a server or a system the attacker can then escalate their privileges by gaining administrator power. There are two ways that you can achieve the administrator power, one is to do an offline attack which in this case you need to gain access to the machine, while the other way to do this is to do an online attack which is an attack from a remote location. Some examples given on offline attack tools include Rainbowcrack, Samdump2, John the ripper, and Ophcrack. Online attack tools include Brutessh, Hydra, TCPDump, Wireshark, and Hamster. You could also use network spoofing tool or also known as Man in the middle attack using Arpspoof and Ettercap.
In this blog we will discuss Target Exploitation and the tool that is used in order to exploit certain information. In this case we will talk about Metasploit. Metasploit is an open source attack framework that is used to hack systems for testing purposes. Why a lot of hackers choose to use Metasploit is because that it is open source and that it is actively updated.
We had a lab assignment using Metasploit using 2 VMs and having one VM control the other VM by shutting it down. Steps will be listed below.

- First step is to boot kali linux and open terminal, then run the msfconsole in the terminal.

2. Using the search command, Search Shellshock and locate the apache_mod_cgi_bash_env_exec Module and copy the location.

3. Type options to see the various settings
4. Check ifconfig on the target vm to get the IP address of the target.

5. The you set the rhost to the target you are trying to attack, set the uri into the directory cgi-bin/status, set the lhost to the current ip of the Virtual Machine that you are using to attack, and lport to your current port. Then run and see if it can be done.

6. Then check ifconfig and see if the IP of the current VM is changed to the one that u were targeting and in this case it changed.
![]()
7. Then do the command to power off the other VM and it works!
Using SET toolkit
In this post we will talk about the lab that required us to create a fake website and when the victim goes to that said website they will be redirected to the website that I made in order to grab their username and password for their facebook account.

- First we check the IP address of the attacker and then proceed by launching Setoolkit and creating our fake website.

2. Choose 1 because we are performing a Social-Engineering attack.

3. Next we choose the option number 2 for Website Attack Vectors.
4. Next we are using the option 3 (Credential Harvester Attack Method).

5. Then we choose the Site Cloner option which is number 2.

6. Then enter the IP address of the attacker and the website that you are trying to clone.

7. Next we start to configure that comes with Kali Linux called Ettercap.
8. Change the Web site that you are using as well with the IP that you are using as you can see in the picture.

9. Next we launch Ettercap.

10. Then we process to Scan for the hosts in Ettercap. Target 1 will be the victim. And Target 2 for getaway.

11. Then we open up the Plugins and Activate DNS Spoof.

12. After doing so we Open up the MITM and activate ARP Poisoning and sniff remote connections.

13. Then we ping facebook.com from the Victim’s machine and as you can see the IP is now directed back to the attackers IP address.

14. Then lastly we go to facebook.com on the victims machine and it will redirect to the cloned site and when entering a username and password. That information will be delivered to the attackers machine to be seen.

In this blog post we will discuss Social Engineering. The point of social engineering is to gain confidential information through human communication. There are a couple ways that we can do this and they are either through an interview or interrogation, and this relies heavily on trust. There are lots of ways to attack a victim with social engineering, some methods include impersonation, reciprocation, influential authority, scarcity, and social relationship. The success rate of social engineering relies on your ability to gain people’s trust and the ability to understand human psychology. Social engineering is probably one of the easiest way to gain confidential information without doing too much work, well just need to be able to communicate well with the victim that you are trying to gather information from.
CA CERTIFICATE / BURPSUITE
In this week we have been given an assignment to create our own CA certificate in order to fool the victim so that they think they website is secured. Here below will be the lab report for that assignment with steps in order how to achieve our goal.


Start Kali Linux and open up the Terminal. Then the first step is to input the command shown in the image above to generate the private key and public key. Then filled in the form with the information required.

After generating the public and private keys then open up Burp Suite. Open the proxy settings and import CA certificate shown in the picture above. Select the files from the Folder where the Public and Private keys are stored. Then import it.

In this case, I have saved the filed into the Home folder. Then import the CA certificate into the web browser.

Then after doing so test if the connection is secure by using the web browser. In this case I tested Google.com and as shown in the picture, the connection is indeed secure. And the CA Certificate is verified.
In this case I named the company Binus and as you can see in the picture that it is verified by Binus.

In this week we discussed the uses of Nmap. Well we first want to know what is Nmap. Nmap is a free open-source network scanner used to discover hosts, locale and remote ports, including network information in a computer network. It is currently the most popular network mappers in the world.
Uses of Nmap:
- Discover hosts
- Create a complete computer network map
- Find remote IP addresses of any hosts
- Get the OS system and software details
- Scan open ports on local and remote systems
- Detect and find vulnerabilities on remote and local hosts
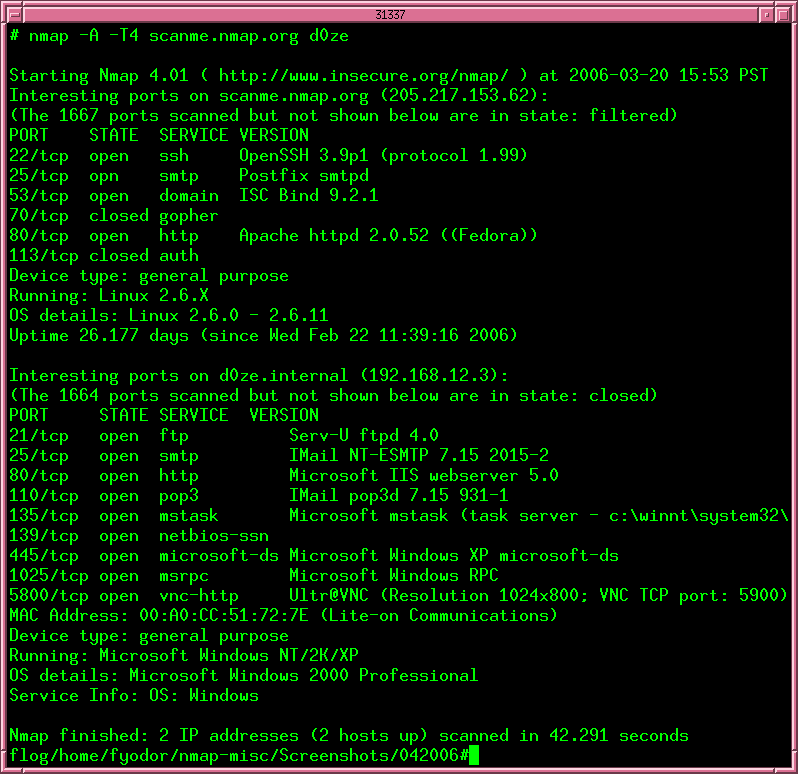
This is the result when using Nmap, and as you can see, there are a list of open ports, Operating system, and MAC address. These information can be very useful to an attacker that knows just how to use them.
We were assigned a lab work to spoof ourselves using a second Virtual Machine and see if we can detect the traffic from the other VM. Here below is the lab report that was made for that assignment.
List of websites I visited.
- Techpanda.org
- Google.com
- BinusMaya
I have visited these websites while spoofing myself. Using only the TCPDump method this time. I tested logging into techpanda.org with a test email and password and then following up by checking on Wireshark to see the http Post and it was there. Will be shown below.

This week we learned to utilize tools in Kali Linux to gather more information on the target that you are trying to expose. For example a tool in Kali Linux called the Harvester can be used in order to gain such valuable information on your target.

In the picture above you can see the Harvester command for searching “cvcc.edu” with the length of 8 from search engine google.
Example Command for the Harvester : theHarvester.py -d targetdomain -l 100 -b google
The harvester is a very powerful tool that can be used for free in Kali Linux. Can be used to gain information from various search engines such as google, bing, yahoo, linkedIn, or twitter.
In the second week we learned about Target Scoping and Information Gathering.
Steps to target scope include :
- Gathering Client Requirements
- Preparing Test Plan
- Profiling Test Boundaries
- Defining Business Objectives
- Project Management & Scheduling
We also discussed Penetration testing types
- White Box Model
- Black Box Model
- Informed Testing
- Social engineering
Also discusses some web tools that can be used in order to gather information.
Some examples are :
Whois : Gives a series of information shown below
In the first week of Ethical Hacking course, we briefly discussed the basics of what hacking is and the cyber laws regarding to hacking. We learned the certificates that are needed in order to be a qualified and ethical hacker. Here is a basic introduction to what we learned on the first meet :
- Ethical hackers
- Employed by companies to perform penetration tests
- Penetration test
- Legal attempt to break into a company’s network to find its weakest link
- Tester only reports findings
- Security test
- More than an attempt to break in; also includes analyzing company’s securitypolicy and procedures
- Tester offers solutions to secure or protect the network
The Instructor Sir Kalpin told his about his career and how his job requires the skills of an Ethical Hacker. He seemed very intellectual and observant regarding to the class that he is teaching. I am looking forward to continue to learn more about ethical hacking in this course.
Recent Comments